Security and Operation System
Teachme Biz Security features help you manage your manuals safely on cloud and work efficiently.
Data Safety
High reliable Data Center

We are using Amazon Web Services (AWS) as a Data Center. AWS is a Data Center with extensive users among domestic as well as international companies. Guaranteed by many certificates obtained from third-party institutions. In addition, the server is installed in Asia Pacific Region.
Regular Data Backup

Data is backed up regularly. When trouble occurs, it is possible to recover the data from backup.
Data Center Redundancy Configuration

It is a redundant configuration using multiple physically separated data centers. This to ensure that data will not be lost due to large-scale disasters.
Operation Safety
Operational framework consistent with international security standards

We acquired “ISO 27001” which is the international standard of Information Security Management System (ISMS) and ISMS cloud security “ISO 2717”, and we operate under strict security standards.
Server monitoring, trouble responding system

Server is being monitored 24 hours a day all year round, and when an abnormality is detected, the person in charge will be notified immediately. Then the person in charge will take a prompt response to restore work according to the situation.
Development Guidelines

By establishing development guidelines internally and conducting work in accordance with the guidelines, we are able to offer a stable and safe service to customers.
Prevention of unauthorized usage and access
Minimum Requirement for Server and Data Management
Access to the server is restricted to Group administrator. Moreover, data stored in the server will be accessed only when requested by the customer for the event such as investigation purpose.
Block Unauthorized Access
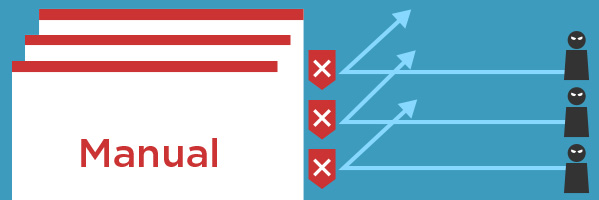
Server access is being monitored constantly and you will be alerted and obtain logs for unauthorized access.
Communication Encryption

Both PC and Mobile versions are using communication encryption by SSL. Even a third party eavesdrops, they cannot understand the contents.
Vulnerability Assessment

We conducted a Web Application vulnerability assessment by a third-party organization, and overall it is evaluated as being strong against unauthorized access (April 2020).
Functions that support Operation Safety
Password and Authority Management
Customer’s Group is managed by password. Furthermore, Group administrator can also set editing and viewing authority of the data within the group.
Device Access Restriction, Access Blocking

Administrator can check access status such as when, who and from which device etc. When the device is being lost or got stolen, you can block the access to that particular device. In addition, any manuals cached inside the device will also be automatically cleared out.
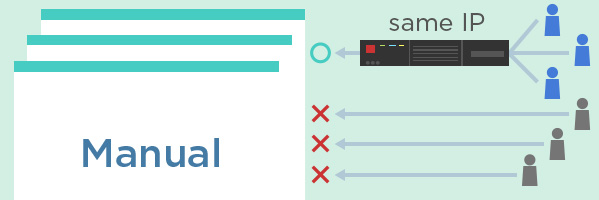
Access Restriction with IP Address